Once you have virtual machines installed and operating within a VirtualBox environment you will probably want to
- connect to the VM guest from the host or
- connect to the host from the VM guests or
- connect one VM to another
For this you need to configure the networking.
Networking set-up can be found in the settings of each VM in the VirtualBox Manager.
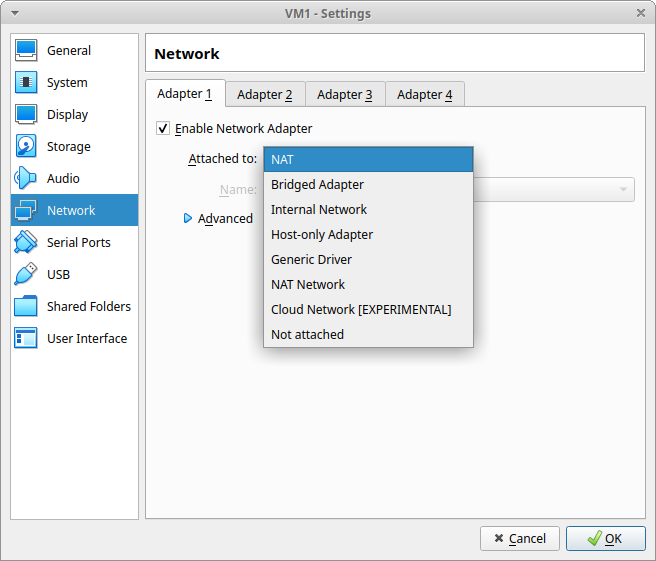
There are number of approaches to VM networking. We’ll be looking at three of them (a fourth option, “not attached”, simply has no network link).
- NAT – Only allows VMs to contact the host & Internet. Nothing inbound.
- Bridged Adapter – Allows inbound and outbound between VM, host & network
- Internal Network – Allows links between VMs only
The usual 3 IP address ranges that are available for private networks (that can’t be directly addressed from the open internet) apply here:
- 10.0.0.0 – 10.255.255.255
- 172.16.0.0 – 172.31.255.255
- 192.168.0.0 – 192.168.255.255
The following is a high level overview of the main options. For the detail, including the likes of virtual network devices and multiple network interfaces per VM, you can check out guides on the web such as this.
NAT
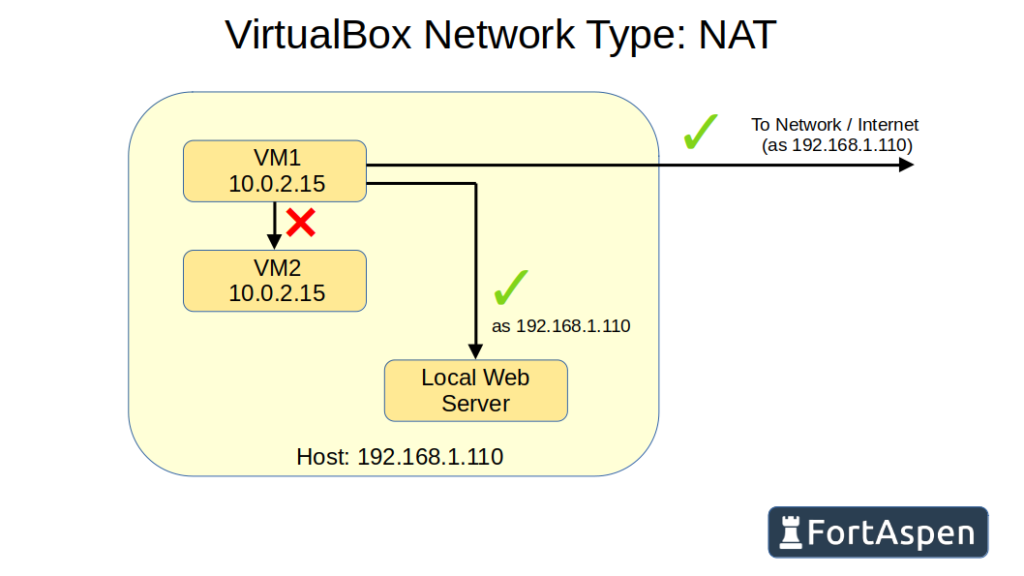
The Network Address Table (NAT) approach holds each VM at arms length from the host and other VMs. The VM is allocated a private IP but that IP is not visible from the host or the wider network.
We created two VMs (hostnames vm1 & vm2) and both were allocated the same private IP: 10.0.2.15.
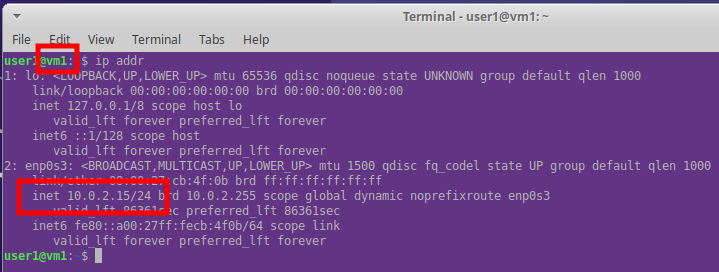
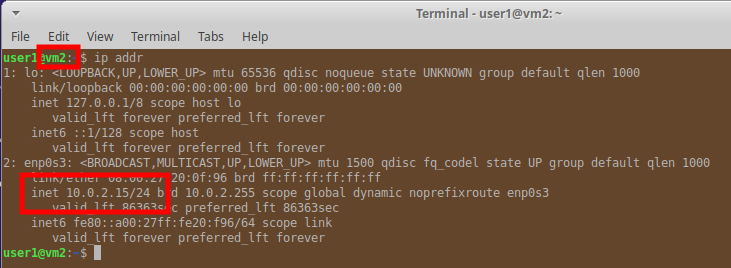
They can communicate out. When a request is made to, for example, www.virtualbox.org, the VirtualBox switches the VM’s IP address with that of the host and passes the request out to the local network. When the response returns VirtualBox intercepts the message and passes it to the requesting VM only.
The host operating system cannot “see” the VM – an attempt to ping that IP from the host is not successful.
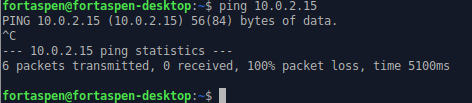
but the VM can request external resources and get a response like this web request.

So a NAT network can have outbound connections but no inbound connections and there is no link between VMs because the all have the same IP.
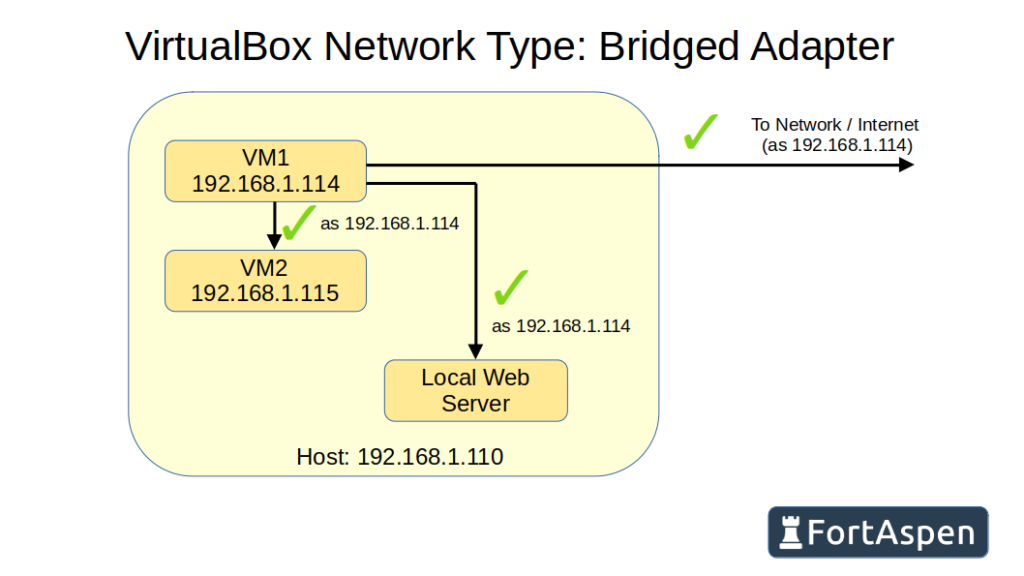
Bridged Adapter
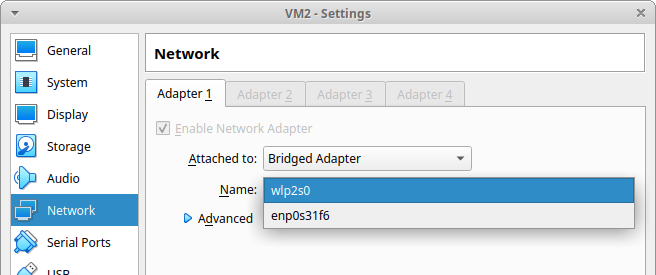
When a VM has a bridged adapter configured, it communicates with the host’s network interface card. You can choose which card in the settings – if you are using a wireless network, don’t choose an unconnected Ethernet card and vice versa.
The VM is allocated an IP from the same source as the host (normally a DHCP server out on the network). Given that the host and the VMs both have valid IPs on the same network, it means they can communicate directly just like any two network devices.
This is a less secure set-up so care should be taken if the network is exposed.
When the VirtualBox networks are configured as a bridged adapter, the IP addresses are obtained from the same range as the host (in this case the host is 192.168.1.110).
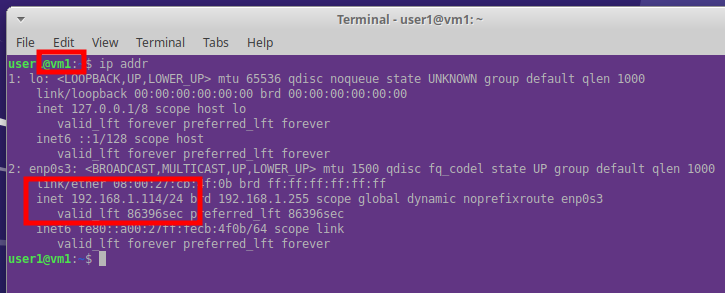
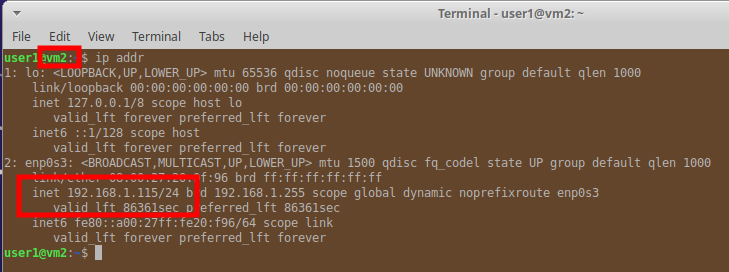
In this case both the VMs have an active web server with a simple html file with the name of the server.
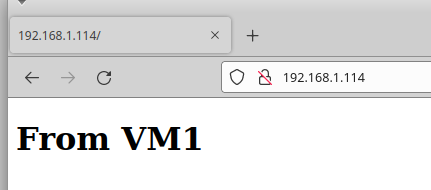
The host can see the VMs.
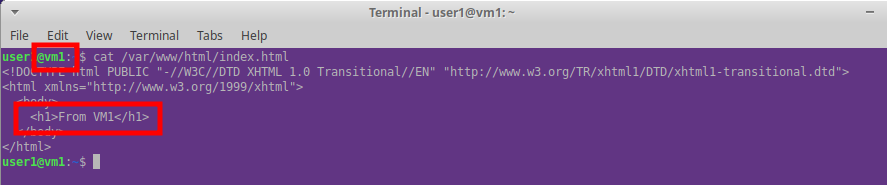
and the VMs can see each other. Here is VM1 looking at VM2.
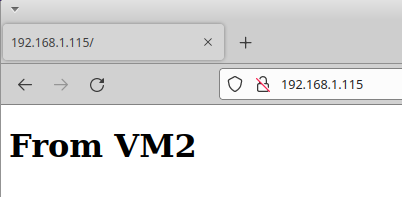
The VMs can also see the host.
So a bridged adapter means the VM behaves much like the host computer with full inbound and outbound links. That does of course mean an attacker can exploit them more readily.
Internal Networking
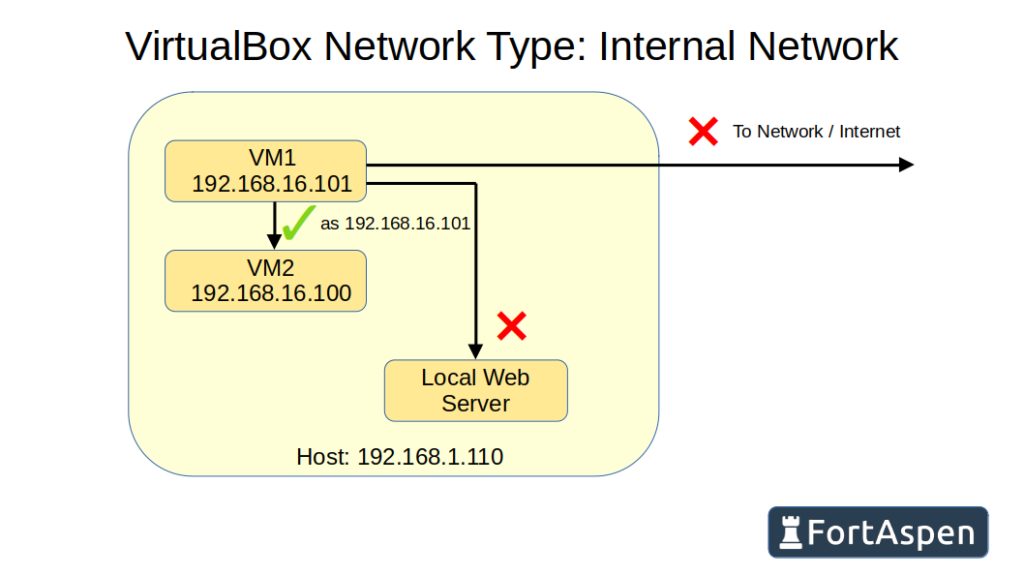
The third alternative is internal network. This aims to let the VMs see each other but not the host or the external network. It is a network internal to VirtualBox.
When you configure a VM to use an internal network you have to give a network name. VMs can only see other VMs with the same network name. This allows different sets of VMs to be on separate independent networks.
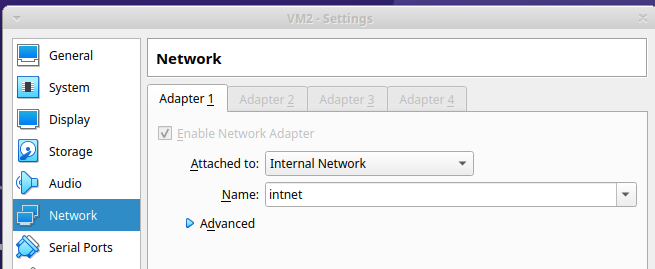
For an internal network to operate you have to either
- manual specify a static IP in the configuration of every VM or
- configure the VirtualBox DHCP service
You can find out about the VirutalBox DHCP service here.
To run the DHCP service, on the host issue the command:
VBoxManage dhcpserver add --netname intnet --ip 192.168.16.1 --netmask 255.255.255.0 --lowerip 192.168.16.100 --upperip 192.168.16.200 --enableThis activates the internal DHCP server with network name “intnet” (which much match the VM configuration above) and allocated IP addresses from 192.168.16.100 → 200.
This results in the VMs getting allocated the following IPs
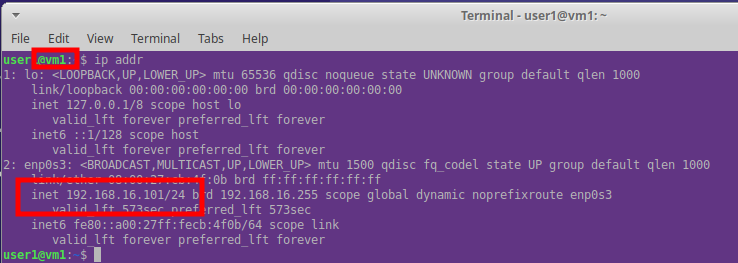
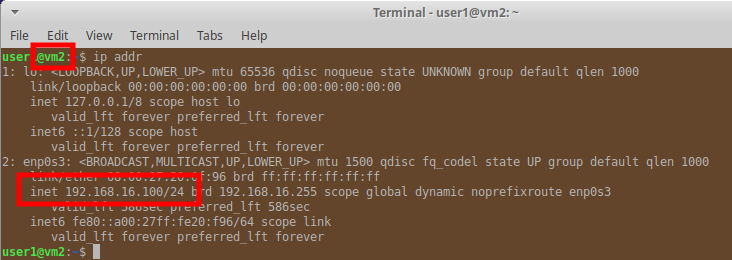
VM1 can see VM2 on the network
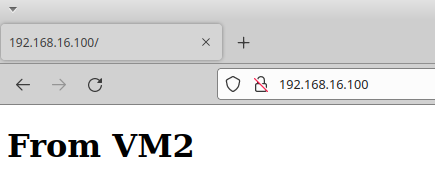
but cannot see the host
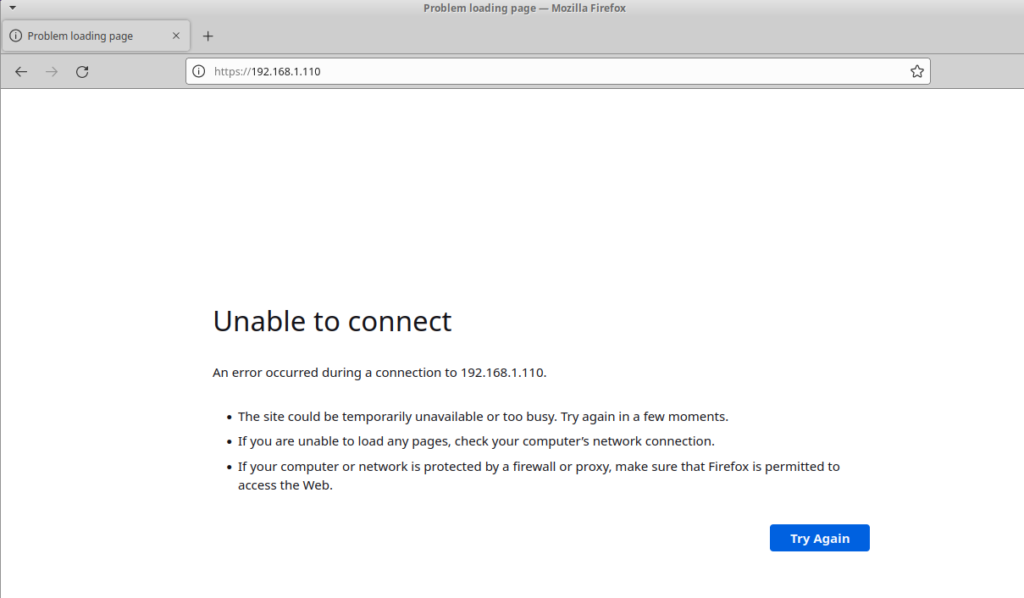
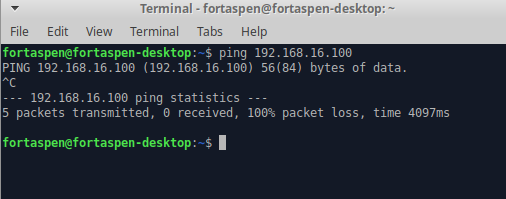
Likewise the host cannot see the VMs.
So an internal network means the VMs are on an isolated network. They can’t connect to the host or the internet (and thus cannot receive software updates) or be accessed from outside their network.