If someone presents you with a certificate saying I’m “amazon.com”, how do you know if that is true? The answer is to get that certificate digitally signed by a “certificate authority” (CA) whom you trust to carefully check the identity of the owner of all the certificates they sign. You can check the signature on the doubtful certificate against the public key certificate of the CA. If the CA did their job and the signature checks out then the certificate can be trusted.
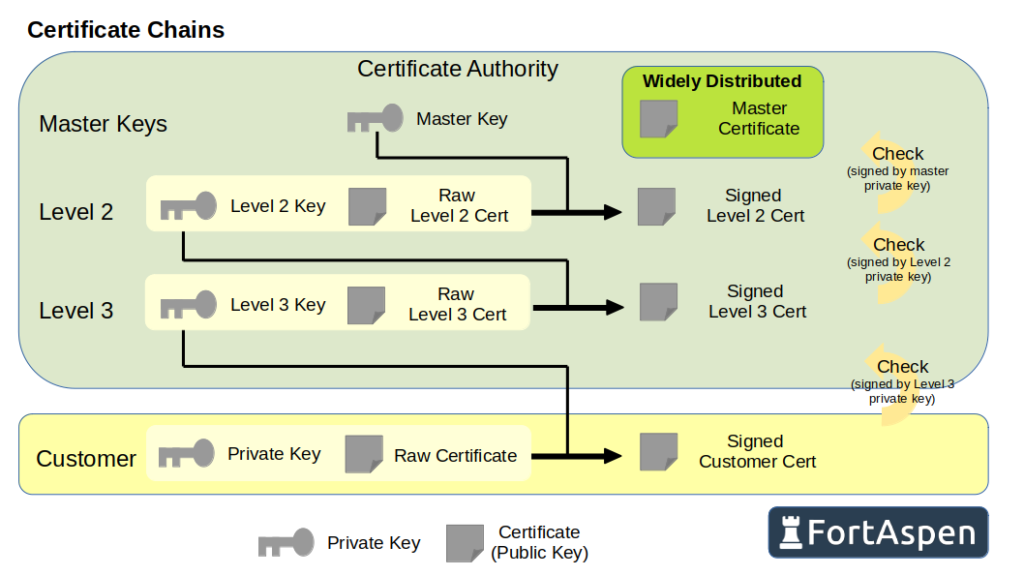
The CA will not sign every customer certificate with a single master certificate. It can create a child CA certificate which is approved/signed by the master CA certificate and then sign customer certificates with that. Certificate checks will then need to (a) check the customer’s certificate against the child CA certificate and then (b) check the child CA certificate against the master CA certificate.
There is no need for this CA hierarchy to stop at two levels it could be any number but note that the certificate checks need access to the whole chain of certificates with each one being checked against the one above it in the hierarchy.
For this to system to work you need to go into the processing holding the master digital certificates (public keys) of the certificate authorities you trust.
Certificate Signing Request
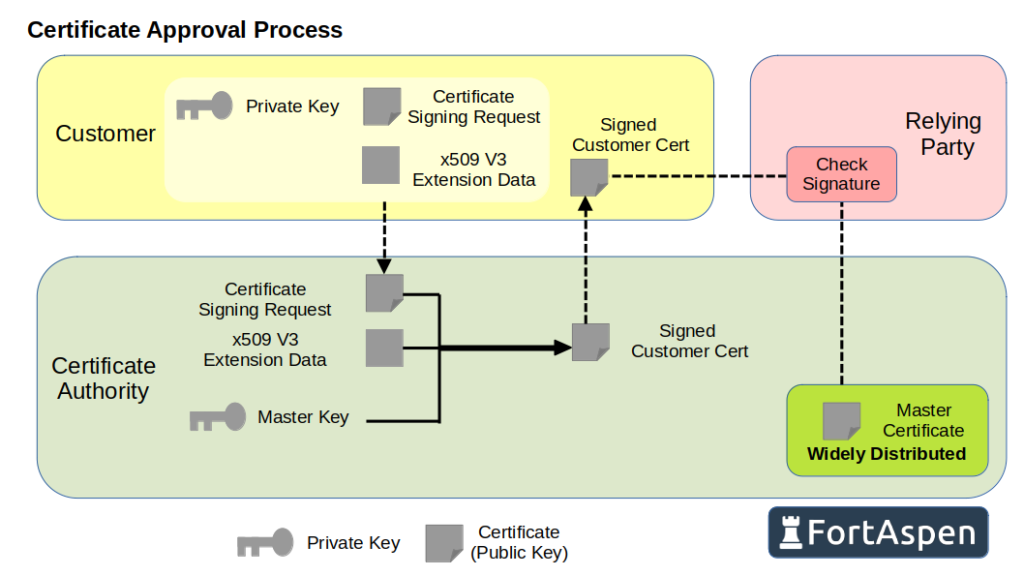
Customers who want a certificate that is signed by the CA must prepare a “Certificate signing request” (CSR) and send this to the certificate authority (not a public key certificate itself).
The basic CSR does not have all the data required for all scenarios. You often have to provide additional information to accompany the CSR, perhaps in a “extension file”.
So the process of obtaining a CA signed certificate becomes:
- Customer prepares CSR (certificate signing request)
- Customer prepares extension data if necessary
- Customer passes CSR & extension data to the certificate authority
- The CA performs checks to confirm the identity of the customer
- If the customer checks are successful, the CA signs the CSR to produce a certificate and returns the signed X509 certificate back to the customer.
To see certificate chains in action, check out our case study of setting up a web server certificate using our own certificate authority.
